Why Zero Knowledge Proofs (ZKPs) is a Game Changer for Self-Sovereign Identity
Discover how Zero Knowledge Proofs (ZKPs) revolutionize decentralized identities, empowering true self-sovereignty and data privacy.
Decentralized and self-sovereign identities are transforming the digital landscape, but have you ever wondered how Zero Knowledge Proofs (ZKPs) are revolutionizing them?
In a time of frequent data breaches and persistent cyberattacks, there is an urgent need to find new ways to verify and manage user identities. Giants like Google, Facebook, and Apple dominate the landscape, collecting vast amounts of user data while retaining the power to revoke access to any account arbitrarily. But the traditional methods of identity management, relying on usernames and passwords, are breeding grounds for data insecurity and reputational risks. By drastically limiting the information centralized institutions possess about us, zero-knowledge proofs pave the way for unparalleled user privacy and the eradication of malicious actions.
In this article, we'll explore the game-changing impact of ZKPs, providing a clear and concise explanation of digital identity, identity systems, verifiable credentials, and the future they hold in self-sovereign identity management. Get ready to dive into the world of ZKPs and unlock a new era of privacy and data security.
What is Zero-Knowledge Proof?
Zero-Knowledge Proof (or ZKP for short) is a method that proves something is what it is or has some features, without revealing those features to a third party. It is applied as an authentication process to prove one possesses private information without giving away any of the information to the verifier.
With zero-knowledge proof, we can confirm if a person of a certain age is qualified for a job without revealing any of their personal information. It proves this piece of information without telling what it is exactly.

There are three main criteria that zero-knowledge proofs must satisfy, namely:
Completeness: The verifier should be able to confirm if the prover is telling the truth.
Soundness: If the information given by the prover is false, the ZKP method must permit the verifier to refute the claim.
Zero Knowledge: The ZKP method must reveal nothing else to the verifier aside from whether the claims are true or not.
Types of Zero Knowledge Proofs
The two types of zero-knowledge proofs are:
1. Interactive Zero Knowledge Proofs
The interactive ZKP requires the proofer to perform a series of actions to convince the verifier of a certain claim. It is more like an interrogation, where the verifier asks more questions to get proof. It is a traditional technique involving repeated processes to convince the verifier that a proof is valid.
2. Non-interactive Zero Knowledge Proofs
Unlike interactive zero-knowledge protocols, where the prover and verifier must interact consistently. Here, one can prove possession of certain claims without any interaction between the prover and verifier.
This form of zero-knowledge proof is applied to the validation of blockchain transactions in ZCash, a cryptocurrency. The transaction information, such as the amount of token sent or received and the wallet address of the sender and recipient, is encrypted cryptographically through Zero-Knowledge Succinct Non-interactive Arguments of Knowledge (ZkSNARKS), a novel form of zero-knowledge that states the claims can be proven valid, or true after multiple trials and certain assumptions.
N/B: The MimbleWimble Extension Blocks (MWEB) function shouldn't be confused with ZKP. The MWEB function gives users the option to transfer confidential Litecoins (a privacy-focused cryptocurrency) without revealing any transaction information such as the sender's wallet address.
Overview of Digital Identity
A digital identity represents the unique characteristics of an individual presented in the form of verifiable credentials by the holder for verification. It can be seen as a claim or distinct information related to a person, institution, or object. For example, certificates, residential address, age, bank account details, driver's licenses, and more.
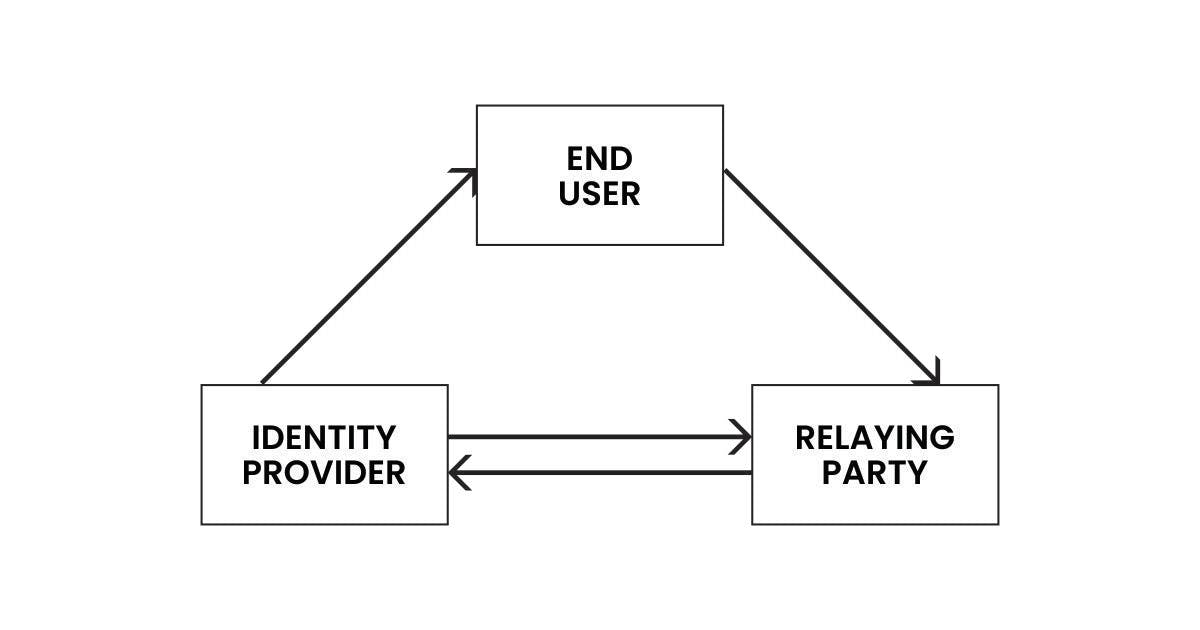
The Trust Triangle Phase
Three entities or key players, namely the issuer, holder, and verifier, must be involved in a phase known as the "Trust Triangle" for a successful identity verification process.
Issuer: This is a trusted entity or organization that provides verifiable credentials (VCs), a digital version of physical identities such as certifications, and identity cards. They provide unique identifiers or claims to an identity holder. An example of an issuer is a university.
Holder: The individual that manages the issued verifiable credentials from the issuer and presents them to a verifier. They have control over their personal information and credentials and can revoke them.
Verifier: This is the institution that seeks proof of the claim's validity presented by the identity owner. They examine the attestation to confirm if the public-private keys of the holder correspond with those on the distributed ledger. An example can be an employer.
Classification of Identity Systems
Identity is classified into the following classes:
- Centralized Identity: This form of identity is in the custody of centralized authorities, who can disclose personal information without obtaining the user's consent, which increases the risk of unauthorized assertions by malicious third parties. This vulnerability often leads to a higher susceptibility to identity theft, cyberattacks, data leaks, and hacks.

- Federated Identity: This is an improvement to centralized identity that enables single sign-on (SSO), the use of a single password to sign in to multiple websites. It depends on an identity provider such as "Sign In with Google", for user authentication on other websites and online services.
- Decentralized Identity: This form of identity uses cryptographic keys where all entities are connected in a network model and unlike the federated identity which depends on a provider model. It gives individuals control over their identity, enabling trusted interactions while preserving privacy. In a decentralized identity system, the user acts as an identity provider by being a holder and presenter of the credentials. The issuer can also be the verifier and vice versa, decomposing the role of the identity provider into an issuer and a holder.
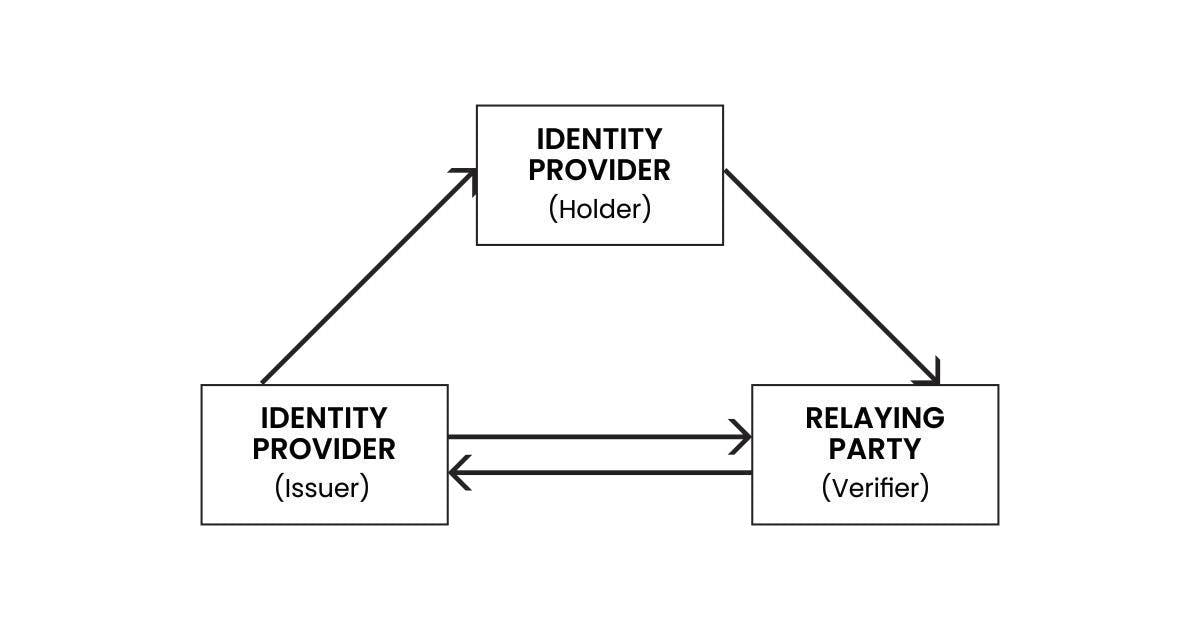
Decentralized identifiers (DIDs) are secured by a private key and are usually associated with an attestation or verifiable credential from the issuer. It also serves as a source of verifiable data used by the user on several platforms without worrying about owning different kinds of identification.
How ZKPs will impact self-sovereign identities and data privacy
In a self-sovereign identity (SSI), the user is the sole custodian of their private keys and information, not relying on the issuer for permission. It lets users own, control, and prove their identity without exposing sensitive information.
Below are some of the ways ZKP will improve self-sovereign identity:
Zero-knowledge proofs empower users to have control over their identity, thereby eliminating the need for KYC (know your customer) requirements.
They enable the provision of verified credentials and proof of ownership of digital assets without the revelation of personal information.
By safeguarding sensitive data and identities, they promote the use of private identities in the form of pseudonymity.
By reinforcing privacy and security, zero-knowledge proofs preserve evidence of private data such as health records, certificates, passports, and credit scores.
They reduce the complexity of encryption methods required to confirm user creditworthiness through their on-chain transactions.
They offer reliable, tamper-proof, and privacy-focused user authentication and access to Web3 applications.
Closing Thoughts
Zero-knowledge proofs revolutionize ownership verification by protecting user privacy without revealing the actual claim. Traceable credentials become a thing of the past as zero-knowledge proofs enable once-issued credentials to evade tracking. While this transformative technology holds immense potential, it does face limitations. Ensuring the accuracy of information and claims requires advanced computational capabilities and iterative processes. However, with continued advancements, zero-knowledge proofs pave the way for a future where users regain control over their digital identities and data.
I hope you liked this article, and if you did, consider following my blog for more content or connecting with me on Twitter.

